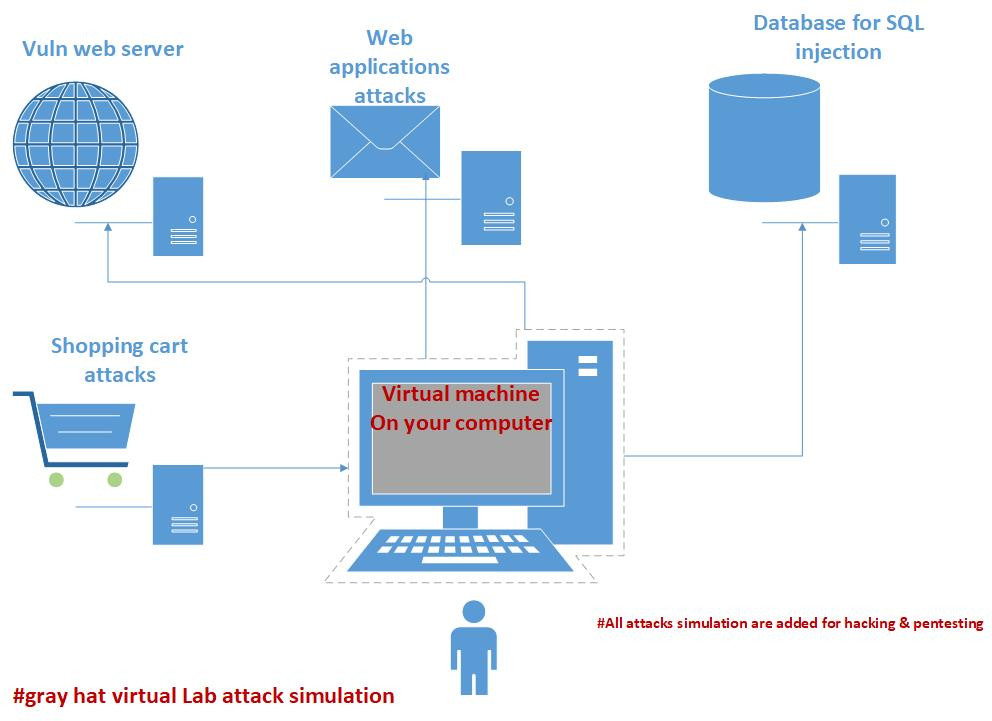
Web App Penetration Testing for Ethical Hacking Definition: Penetration Testing Professional process to model techniques of real world attackers on a defined target to find and exploit vulnerabilities for the purpose of improving security. Makes use of and includes ethical hacking techniques. Has a more limited focus and is a subset of Ethical Hacking.
Complete Ethical Hacking and Penetration Testing for Web
Web Application Penetration Testing Training SANS SEC542. Penetration testers Ethical hackers Web application developers Website designers and architects You Will Be Able To Apply a detailed, four-step methodology to your web application penetration tests: reconnaissance, mapping, discovery, and exploitation Analyze the results from automated web testing …, Build your defense against web attacks with Kali Linux, including command injection flaws, crypto implementation layers, and web application security holes About This Book Know how to set up your … - Selection from Web Penetration Testing with Kali Linux - Third Edition [Book].
Web Application Penetration Testing Tutorial Playlist Ethical Hacking & Penetration Testing - Complete Course Play all. Ethical Hacking & Penetration Testing Course hackersploit,hacking,kali Becoming the Hacker will teach you how to approach web penetration testing with an attacker's mindset. While testing web applications for performance is common, the ever-changing threat landscape makes security testing much more difficult for the defender.
18/07/2018В В· From the start of the book, you'll be given a thorough grounding in the concepts of hacking and penetration testing, and you'll see the tools used in Kali Linux that relate to web application hacking. You'll gain a deep understanding of classicalSQL, command-injection flaws, and the many ways to exploit these flaws. Web penetration testing also needs a general overview of client-side attacks Becoming the Hacker will teach you how to approach web penetration testing with an attacker's mindset. While testing web applications for performance is common, the ever-changing threat landscape makes security testing much more difficult for the defender.
Home. bWAPP, or a buggy web application, is a free and open source deliberately insecure web application. It helps security enthusiasts, developers and students to discover and to prevent web vulnerabilities. bWAPP prepares one to conduct successful penetration testing and ethical hacking projects. What makes bWAPP so unique? You'll gain insight into the insecurities, vulnerabilities and exploits that lie within web applications so you can reduce the risk this poses to your business. This CREST Accredited course is based on OWASP Top 10 2017 and along with course Network Infrastructure Penetration Testing and Ethical Hacking will help students prepare for the CREST CRT examination.
Learn to test a web application or test a cloud-based application in an API based application. About : In this course, we will be concentrating mainly on how Penetration Testing can be done on web-based applications. And it can also be used for mobile-based applications because most of the mobile-based applications communicate with a cloud The most accurate way to know your organizational weaknesses is to examine your business environment the way a hacker would-- through manual security penetration testing, also called ethical hacking. Our certified penetration testers use up-to-date hacking methodologies and innovative technology to identify vulnerabilities, minimize risk, and
This cheat sheet is from our SANS SEC560: Network Penetration Testing and Ethical Hacking course, authored by SANS Fellow, Ed Skoudis. To learn Netcat in-depth along with many other tools, methods, and techniques of penetration testing, please consider taking our core pen testing course, SEC560. What is Netcat... from the wiki: You'll gain insight into the insecurities, vulnerabilities and exploits that lie within web applications so you can reduce the risk this poses to your business. This CREST Accredited course is based on OWASP Top 10 2017 and along with course Network Infrastructure Penetration Testing and Ethical Hacking will help students prepare for the CREST CRT examination.
Penetration testing and ethical hacking are skill sets as in-demand as anything else in the Cyber Security industry. Previous to Cybrary, this type of training was very expensive, and now it is free. Anyone who wants to become a penetration tester, ethical hacker (CEH), … 18/07/2018 · From the start of the book, you'll be given a thorough grounding in the concepts of hacking and penetration testing, and you'll see the tools used in Kali Linux that relate to web application hacking. You'll gain a deep understanding of classicalSQL, command-injection flaws, and the many ways to exploit these flaws. Web penetration testing also needs a general overview of client-side attacks
Web App Penetration Testing and Ethical Hacking.tar.gz SANS 560 - Network Penetration Testing and Ethical Hacking.tar.gz . CISSP Study Guide- 7th Edition.pdf. Penetration Testing and Ethical Hacking; . Download Here. . Over 300 tools are available for purchase in the catalog via the Cybrary Vendor network.. Develop a penetration test plan . Such strategies lead to games biased in favor of the Definition: Penetration Testing Professional process to model techniques of real world attackers on a defined target to find and exploit vulnerabilities for the purpose of improving security. Makes use of and includes ethical hacking techniques. Has a more limited focus and is a subset of Ethical Hacking.
Hello and welcome to Web Based Ethical Hacking and Penetration Testing for Beginners. Internet is all around us. We have been using the facilities of internet since a long while and as the internet came in, the cyber-security threat also started to appear. You can hear stories of cyber-attacks day by day in news papers and media. Want to test your Website and Web Application? In addition to the Open Source Security Testing Methodology Manual (OSSTMM) and the Penetration Testing Execution Standard (PTES) Black Hat Ethical Hacking’s penetration testing service leverages the Open Web Application Security Project (OWASP), a comprehensive framework for assessing the security of web-based applications, as a …
You'll gain insight into the insecurities, vulnerabilities and exploits that lie within web applications so you can reduce the risk this poses to your business. This CREST Accredited course is based on OWASP Top 10 2017 and along with course Network Infrastructure Penetration Testing and Ethical Hacking will help students prepare for the CREST CRT examination. You'll gain insight into the insecurities, vulnerabilities and exploits that lie within web applications so you can reduce the risk this poses to your business. This CREST Accredited course is based on OWASP Top 10 2017 and along with course Network Infrastructure Penetration Testing and Ethical Hacking will help students prepare for the CREST CRT examination.
Penetration Testing is the process of assessing or testing technology to find any weaknesses that can be exploited by hackers. It is sometimes referred to as Ethical Hacking or Hack Testing. Testing is performed under strict controls to ensure that disruption is kept to a minimum. This paper explores the ethics behind ethical hacking and whether there are problems that lie with this new field of work. Since ethical hacking has been a controversial subject over the past few
Download 100 Free Hacking Book Collection 2018 ETHICAL. Penetration Testing Courseware. The Virtual Hacking Labs Ethical hacking and Penetration Testing courseware covers a wide range of subjects that will teach you everything about penetration testing. Each section of the courseware covers basic theory and practical demonstrations of techniques making it very beginner friendly. After going through, Practical Web Penetration Testing is for you if you are a security professional, penetration tester, or stakeholder who wants to execute penetration testing using the latest and most popular tools. Basic knowledge of ethical hacking would be an added advantage..
SANS Penetration Testing SANS Cheat Sheet Netcat SANS

Penetration testing course Virtual Hacking Labs. We’ve designed a complete penetration/hacking course just for you! Hacker is often seen as someone who performs illegal intrusions into a computing system to steal money and/or information from the owner for their own gains. However, there is also some thing known as Ethical Hacking. This hacking, also known as penetration testing, isn’t, Advanced Penetration Testing Hacking 2017.pdf 2. CEH v9 Certified Ethical Hacker Version 9.pdf 3. Begin Ethical Hacking with Python.pdf […] CEH v9 Certified Ethical Hacker Version 9.pdf 3. Begin Ethical Hacking with Python.pdf […].
Graduate Certificate Program Penetration Testing & Ethical. Learn Ethical Hacking Online. Learn Ethical Hacking Online. Toggle navigation Home My Courses All Courses Sample Certificate Login Sign Up Ethical Hacking & Web Application Penetration Testing 2 Courses / 30Hrs / 160+ Videos / Life Term access and Support Watch Promo Enroll in Course for $15 ×, We’ve designed a complete penetration/hacking course just for you! Hacker is often seen as someone who performs illegal intrusions into a computing system to steal money and/or information from the owner for their own gains. However, there is also some thing known as Ethical Hacking. This hacking, also known as penetration testing, isn’t.
Learn Ethical Hacking and Penetration Testing using Android
Ethical Hacking 101 Web App Penetration Testing a full. Overall: I had the opportunity to take SANS SEC542 Web Application Penetration Testing & Ethical Hacking during the SANS Cyber Defense Initiative (CDI) event in Washington D.C. this December with one of the course authors Eric Conrad.Eric absolutely killed it, and was one of the reasons I signed up for this particular course. I had heard he was a great speaker and had lots of relevant https://en.m.wikipedia.org/wiki/White_hat_(computer_security) limiting factor on what we are able to create with information technology. At The Open Web Application Security Project (OWASP), we're trying to make the world a place where insecure software is the anomaly, not the norm, and the OWASP Testing Guide is an important piece of the puzzle..

This cheat sheet is from our SANS SEC560: Network Penetration Testing and Ethical Hacking course, authored by SANS Fellow, Ed Skoudis. To learn Netcat in-depth along with many other tools, methods, and techniques of penetration testing, please consider taking our core pen testing course, SEC560. What is Netcat... from the wiki: 23/07/2019 · Web Penetration Testing with Kali Linux – Third Edition: Explore the methods and tools of ethical hacking with Kali Linux Build your defense against web attacks with Kali Linux, including command injection flaws, crypto implementation layers, and web application security holes
Graduate Certificate Program Penetration Testing & Ethical Hacking The SANS Technology Institute’s post-baccalaureate certificate program in Penetration Testing & Ethical Hacking is based entirely upon courses already available as an elective path through its graduate program leading to a Master of Science Degree in Information Security Engineering. As an independent offering, the graduate The most accurate way to know your organizational weaknesses is to examine your business environment the way a hacker would-- through manual security penetration testing, also called ethical hacking. Our certified penetration testers use up-to-date hacking methodologies and innovative technology to identify vulnerabilities, minimize risk, and
This tutorial is about testing penetration and ethical hacking, designed to students. Free training document in PDF under 47 pages by Dr. Bruce V. Hartley. Web App Penetration Testing and Ethical Hacking.tar.gz SANS 560 - Network Penetration Testing and Ethical Hacking.tar.gz . CISSP Study Guide- 7th Edition.pdf. Penetration Testing and Ethical Hacking; . Download Here. . Over 300 tools are available for purchase in the catalog via the Cybrary Vendor network.. Develop a penetration test plan . Such strategies lead to games biased in favor of the
Build your defense against web attacks with Kali Linux, including command injection flaws, crypto implementation layers, and web application security holes About This Book Know how to set up your … - Selection from Web Penetration Testing with Kali Linux - Third Edition [Book] Learn to test a web application or test a cloud-based application in an API based application. About : In this course, we will be concentrating mainly on how Penetration Testing can be done on web-based applications. And it can also be used for mobile-based applications because most of the mobile-based applications communicate with a cloud
23/07/2019 · Web Penetration Testing with Kali Linux – Third Edition: Explore the methods and tools of ethical hacking with Kali Linux Build your defense against web attacks with Kali Linux, including command injection flaws, crypto implementation layers, and web application security holes Practical Web Penetration Testing is for you if you are a security professional, penetration tester, or stakeholder who wants to execute penetration testing using the latest and most popular tools. Basic knowledge of ethical hacking would be an added advantage.
Penetration testers Ethical hackers Web application developers Website designers and architects You Will Be Able To Apply a detailed, four-step methodology to your web application penetration tests: reconnaissance, mapping, discovery, and exploitation Analyze the results from automated web testing … Penetration testing is very closely related to ethical hacking, so these two terms are often used interchangeably. However there is a thin line of difference between these two terms. This chapter provides insights into some basic concepts and fundamental differences between penetration testing and
Instead, they need to understand how these tools work in-depth, and conduct their test in a careful, professional manner. This course explains the inner workings of numerous tools and their use in effective network penetration testing and ethical hacking projects." Read More Web applications play a vital role in every modern organization. But, if your organization does not properly test and secure its web apps, adversaries can compromise these applications, damage business functionality, and steal data. Unfortunately, many organizations operate under the mistaken impression that a web application security scanner will reliably discover flaws in
Penetration testers Ethical hackers Web application developers Website designers and architects You Will Be Able To Apply a detailed, four-step methodology to your web application penetration tests: reconnaissance, mapping, discovery, and exploitation Analyze the results from automated web testing … Advanced Penetration Testing Hacking 2017.pdf 2. CEH v9 Certified Ethical Hacker Version 9.pdf 3. Begin Ethical Hacking with Python.pdf […] CEH v9 Certified Ethical Hacker Version 9.pdf 3. Begin Ethical Hacking with Python.pdf […]
23/07/2019 · Web Penetration Testing with Kali Linux – Third Edition: Explore the methods and tools of ethical hacking with Kali Linux Build your defense against web attacks with Kali Linux, including command injection flaws, crypto implementation layers, and web application security holes Web Application Penetration Testing Tutorial Playlist Ethical Hacking & Penetration Testing - Complete Course Play all. Ethical Hacking & Penetration Testing Course hackersploit,hacking,kali
Here is a collection of Best Ethical Hacking PDF Books.Download Hacking Books In PDF and learn best hacking tutorials 2017. There are many ways to Learn Ethical Hacking like you can learn to hack from online websites, learn from Hacking books.So here is the list of all best hacking books free download in PDF … Penetration testers Ethical hackers Web application developers Website designers and architects You Will Be Able To Apply a detailed, four-step methodology to your web application penetration tests: reconnaissance, mapping, discovery, and exploitation Analyze the results from automated web testing …

Web Application Penetration Testing. In this course, Cybrary subject matter expert, Raymond Evans, takes you on a wild and fascinating journey into the cyber security discipline of web application … Practical Web Penetration Testing is for you if you are a security professional, penetration tester, or stakeholder who wants to execute penetration testing using the latest and most popular tools. Basic knowledge of ethical hacking would be an added advantage.
Ethical Hacking 101 Web App Penetration Testing a full

Certified Ethical Hacker EC-Council. Practical Web Penetration Testing is for you if you are a security professional, penetration tester, or stakeholder who wants to execute penetration testing using the latest and most popular tools. Basic knowledge of ethical hacking would be an added advantage., Web applications play a vital role in every modern organization. But, if your organization does not properly test and secure its web apps, adversaries can compromise these applications, damage business functionality, and steal data. Unfortunately, many organizations operate under the mistaken impression that a web application security scanner will reliably discover flaws in.
Penetration Testing Ethical Hacking SecurityMetrics
SANS – SEC542 Web App Penetration Testing and Ethical Hacking. Penetration testers Ethical hackers Web application developers Website designers and architects You Will Be Able To Apply a detailed, four-step methodology to your web application penetration tests: reconnaissance, mapping, discovery, and exploitation Analyze the results from automated web testing …, Instead, they need to understand how these tools work in-depth, and conduct their test in a careful, professional manner. This course explains the inner workings of numerous tools and their use in effective network penetration testing and ethical hacking projects." Read More.
This paper explores the ethics behind ethical hacking and whether there are problems that lie with this new field of work. Since ethical hacking has been a controversial subject over the past few The most accurate way to know your organizational weaknesses is to examine your business environment the way a hacker would-- through manual security penetration testing, also called ethical hacking. Our certified penetration testers use up-to-date hacking methodologies and innovative technology to identify vulnerabilities, minimize risk, and
Web applications play a vital role in every modern organization. But, if your organization does not properly test and secure its web apps, adversaries can compromise these applications, damage business functionality, and steal data. Unfortunately, many organizations operate under the mistaken impression that a web application security scanner will reliably discover flaws in Becoming the Hacker will teach you how to approach web penetration testing with an attacker's mindset. While testing web applications for performance is common, the ever-changing threat landscape makes security testing much more difficult for the defender.
Web App Penetration Testing and Ethical Hacking.tar.gz SANS 560 - Network Penetration Testing and Ethical Hacking.tar.gz . CISSP Study Guide- 7th Edition.pdf. Penetration Testing and Ethical Hacking; . Download Here. . Over 300 tools are available for purchase in the catalog via the Cybrary Vendor network.. Develop a penetration test plan . Such strategies lead to games biased in favor of the Overall: I had the opportunity to take SANS SEC542 Web Application Penetration Testing & Ethical Hacking during the SANS Cyber Defense Initiative (CDI) event in Washington D.C. this December with one of the course authors Eric Conrad.Eric absolutely killed it, and was one of the reasons I signed up for this particular course. I had heard he was a great speaker and had lots of relevant
Penetration Testing is the process of assessing or testing technology to find any weaknesses that can be exploited by hackers. It is sometimes referred to as Ethical Hacking or Hack Testing. Testing is performed under strict controls to ensure that disruption is kept to a minimum. Graduate Certificate Program Penetration Testing & Ethical Hacking The SANS Technology Institute’s post-baccalaureate certificate program in Penetration Testing & Ethical Hacking is based entirely upon courses already available as an elective path through its graduate program leading to a Master of Science Degree in Information Security Engineering. As an independent offering, the graduate
limiting factor on what we are able to create with information technology. At The Open Web Application Security Project (OWASP), we're trying to make the world a place where insecure software is the anomaly, not the norm, and the OWASP Testing Guide is an important piece of the puzzle. Web Application Penetration Testing. In this course, Cybrary subject matter expert, Raymond Evans, takes you on a wild and fascinating journey into the cyber security discipline of web application …
This paper explores the ethics behind ethical hacking and whether there are problems that lie with this new field of work. Since ethical hacking has been a controversial subject over the past few 02/09/2015В В· Description. This course introduces ethical hackers and penetration testers to Kali Linux. This course will show IT professionals how to use the ethical hacking techniques and how to conduct a professional penetration test workflow using the Swiss Army Knife operating system Kali Linux.
02/09/2015В В· Description. This course introduces ethical hackers and penetration testers to Kali Linux. This course will show IT professionals how to use the ethical hacking techniques and how to conduct a professional penetration test workflow using the Swiss Army Knife operating system Kali Linux. This course is 5 courses bundled as single course title "Learn Ethical Hacking: Entry to Expertise Level: 5 Courses Pack" the biggest Course to Make You MASTERS in Hacking,Courses covers from basics to advanced levels of Web & mobile apps pen-testing. Course 1: Ethical Hacking. Course 2: Web Application Penetration Testing
Instead, they need to understand how these tools work in-depth, and conduct their test in a careful, professional manner. This course explains the inner workings of numerous tools and their use in effective network penetration testing and ethical hacking projects." Read More Home. bWAPP, or a buggy web application, is a free and open source deliberately insecure web application. It helps security enthusiasts, developers and students to discover and to prevent web vulnerabilities. bWAPP prepares one to conduct successful penetration testing and ethical hacking projects. What makes bWAPP so unique?
limiting factor on what we are able to create with information technology. At The Open Web Application Security Project (OWASP), we're trying to make the world a place where insecure software is the anomaly, not the norm, and the OWASP Testing Guide is an important piece of the puzzle. Graduate Certificate Program Penetration Testing & Ethical Hacking The SANS Technology Institute’s post-baccalaureate certificate program in Penetration Testing & Ethical Hacking is based entirely upon courses already available as an elective path through its graduate program leading to a Master of Science Degree in Information Security Engineering. As an independent offering, the graduate
Home. bWAPP, or a buggy web application, is a free and open source deliberately insecure web application. It helps security enthusiasts, developers and students to discover and to prevent web vulnerabilities. bWAPP prepares one to conduct successful penetration testing and ethical hacking projects. What makes bWAPP so unique? SANS has stepped up to the plate and re-released SEC542 Web App Penetration Testing and Ethical Hacking as a 6-day course with stronger hands-on exercises and culminating with a final day where students perform a penetration test on the classroom network.
Practical Web Penetration Testing [Book]

Web App Penetration Testing for Ethical Hacking. 12/12/2018В В· Learn web application penetration testing from beginner to advanced. This course is perfect for people who are interested in cybersecurity or ethical hacking. вђпёЏResourcesвђпёЏ Burp Suite, Penetration Testing Courseware. The Virtual Hacking Labs Ethical hacking and Penetration Testing courseware covers a wide range of subjects that will teach you everything about penetration testing. Each section of the courseware covers basic theory and practical demonstrations of techniques making it very beginner friendly. After going through.
Web App Penetration Testing and Ethical Hacking. Penetration Testing Courseware. The Virtual Hacking Labs Ethical hacking and Penetration Testing courseware covers a wide range of subjects that will teach you everything about penetration testing. Each section of the courseware covers basic theory and practical demonstrations of techniques making it very beginner friendly. After going through, An Overview of Penetration Testing Article (PDF Available) in International Journal of Network Security & Its Applications 3(6):19-38 В· November 2011 with 13,540 Reads How we measure 'reads'.
HackerSploit YouTube

Complete Ethical Hacking and Penetration Testing for Web. limiting factor on what we are able to create with information technology. At The Open Web Application Security Project (OWASP), we're trying to make the world a place where insecure software is the anomaly, not the norm, and the OWASP Testing Guide is an important piece of the puzzle. https://en.wikipedia.org/wiki/ImmuniWeb 18/07/2018В В· From the start of the book, you'll be given a thorough grounding in the concepts of hacking and penetration testing, and you'll see the tools used in Kali Linux that relate to web application hacking. You'll gain a deep understanding of classicalSQL, command-injection flaws, and the many ways to exploit these flaws. Web penetration testing also needs a general overview of client-side attacks.

SANS has stepped up to the plate and re-released SEC542 Web App Penetration Testing and Ethical Hacking as a 6-day course with stronger hands-on exercises and culminating with a final day where students perform a penetration test on the classroom network. This paper explores the ethics behind ethical hacking and whether there are problems that lie with this new field of work. Since ethical hacking has been a controversial subject over the past few
We’ve designed a complete penetration/hacking course just for you! Hacker is often seen as someone who performs illegal intrusions into a computing system to steal money and/or information from the owner for their own gains. However, there is also some thing known as Ethical Hacking. This hacking, also known as penetration testing, isn’t Graduate Certificate Program Penetration Testing & Ethical Hacking The SANS Technology Institute’s post-baccalaureate certificate program in Penetration Testing & Ethical Hacking is based entirely upon courses already available as an elective path through its graduate program leading to a Master of Science Degree in Information Security Engineering. As an independent offering, the graduate
> About PENTESTING: Penetration testing (also called pen testing) is the practice of testing a computer system, network or Web application to find vulnerabilities that an attacker could exploit. > FIVE PHASES OF PENTESTING : Phase 1 Reconnaissa... Web applications play a vital role in every modern organization. But, if your organization does not properly test and secure its web apps, adversaries can compromise these applications, damage business functionality, and steal data. Unfortunately, many organizations operate under the mistaken impression that a web application security scanner will reliably discover flaws in
Penetration Testing Courseware. The Virtual Hacking Labs Ethical hacking and Penetration Testing courseware covers a wide range of subjects that will teach you everything about penetration testing. Each section of the courseware covers basic theory and practical demonstrations of techniques making it very beginner friendly. After going through Penetration testing and ethical hacking are skill sets as in-demand as anything else in the Cyber Security industry. Previous to Cybrary, this type of training was very expensive, and now it is free. Anyone who wants to become a penetration tester, ethical hacker (CEH), …
Overall: I had the opportunity to take SANS SEC542 Web Application Penetration Testing & Ethical Hacking during the SANS Cyber Defense Initiative (CDI) event in Washington D.C. this December with one of the course authors Eric Conrad.Eric absolutely killed it, and was one of the reasons I signed up for this particular course. I had heard he was a great speaker and had lots of relevant Build your defense against web attacks with Kali Linux, including command injection flaws, crypto implementation layers, and web application security holes About This Book Know how to set up your … - Selection from Web Penetration Testing with Kali Linux - Third Edition [Book]
Penetration testing and ethical hacking are skill sets as in-demand as anything else in the Cyber Security industry. Previous to Cybrary, this type of training was very expensive, and now it is free. Anyone who wants to become a penetration tester, ethical hacker (CEH), … Here is a collection of Best Ethical Hacking PDF Books.Download Hacking Books In PDF and learn best hacking tutorials 2017. There are many ways to Learn Ethical Hacking like you can learn to hack from online websites, learn from Hacking books.So here is the list of all best hacking books free download in PDF …
This cheat sheet is from our SANS SEC560: Network Penetration Testing and Ethical Hacking course, authored by SANS Fellow, Ed Skoudis. To learn Netcat in-depth along with many other tools, methods, and techniques of penetration testing, please consider taking our core pen testing course, SEC560. What is Netcat... from the wiki: SANS – SEC542: Web App Penetration Testing and Ethical Hacking English Size: 485.53 MB Category: Security/Hacking Web applications play a vital role in every modern organization. But, if your organization does not properly test and secure its web apps, adversaries can compromise these applications, damage business functionality, and steal
This paper explores the ethics behind ethical hacking and whether there are problems that lie with this new field of work. Since ethical hacking has been a controversial subject over the past few Web Application Penetration Testing Tutorial Playlist Ethical Hacking & Penetration Testing - Complete Course Play all. Ethical Hacking & Penetration Testing Course hackersploit,hacking,kali
Advanced Penetration Testing Hacking 2017.pdf 2. CEH v9 Certified Ethical Hacker Version 9.pdf 3. Begin Ethical Hacking with Python.pdf […] CEH v9 Certified Ethical Hacker Version 9.pdf 3. Begin Ethical Hacking with Python.pdf […] The most accurate way to know your organizational weaknesses is to examine your business environment the way a hacker would-- through manual security penetration testing, also called ethical hacking. Our certified penetration testers use up-to-date hacking methodologies and innovative technology to identify vulnerabilities, minimize risk, and
> About PENTESTING: Penetration testing (also called pen testing) is the practice of testing a computer system, network or Web application to find vulnerabilities that an attacker could exploit. > FIVE PHASES OF PENTESTING : Phase 1 Reconnaissa... Penetration testers Ethical hackers Web application developers Website designers and architects You Will Be Able To Apply a detailed, four-step methodology to your web application penetration tests: reconnaissance, mapping, discovery, and exploitation Analyze the results from automated web testing …

Becoming the Hacker will teach you how to approach web penetration testing with an attacker's mindset. While testing web applications for performance is common, the ever-changing threat landscape makes security testing much more difficult for the defender. Practical Web Penetration Testing is for you if you are a security professional, penetration tester, or stakeholder who wants to execute penetration testing using the latest and most popular tools. Basic knowledge of ethical hacking would be an added advantage.