Cyber security management a governance risk and compliance framework pdf Kings Tableland

Security Risk Management an overview ScienceDirect Topics to maintain a cyber environment that encourages efficiency, innovation, and economic prosperity to apply the principles and best practices of risk management to improving the security and resilience of critical infrastructure. The Framework provides characteristics defined in the Framework (e.g., risk and threat aware, repeatable, and
Framework on Information Technology Governance & Risk
Governance Risk and Compliance Cyber Security Software. Continuum GRC is #1 ranked Governance Risk and Compliance Software. Get the most efficient, cost-effective cyber security tool, 888-896-6207., Information Security Governance: Toward a Framework for Action reports, laws and regulations. According to Carnegie Mellon University’s CERT Coordination Center, the quantity of cyber security incidents reported has roughly doubled every year since 2000 – jumping from nearly 22,000 sound risk management practices at the operational.
Companies must figure out how to achieve an efficient and effective control framework for global cybersecurity compliance. Global cybersecurity compliance integrity Download the PDF. More similar than different Notice on Technology Risk Management 1 (Singapore). This notice is issued pursuant to section 55 of the Banking Act (Cap. Companies must figure out how to achieve an efficient and effective control framework for global cybersecurity compliance. Global cybersecurity compliance integrity Download the PDF. More similar than different Notice on Technology Risk Management 1 (Singapore). This notice is issued pursuant to section 55 of the Banking Act (Cap.
Mar 23, 2018В В· Cyber Security Management: A Governance, Risk and Compliance Framework - Kindle edition by Peter Trim, Yang-Im Lee. Download it once and read it on your Kindle device, PC, phones or tablets. Use features like bookmarks, note taking and highlighting while reading Cyber Security Management: A Governance, Risk and Compliance Framework. Information security governance is a subset of corporate governance that provides strategic direction for security activities and ensures that cybersecurity objectives such as effective risk and
Information Security Governance: Toward a Framework for Action reports, laws and regulations. According to Carnegie Mellon University’s CERT Coordination Center, the quantity of cyber security incidents reported has roughly doubled every year since 2000 – jumping from nearly 22,000 sound risk management practices at the operational “Governance, Risk and Compliance is a unique segment of the cybersecurity industry” says Steve Morgan, founder and Editor-In-Chief at Cybersecurity Ventures. “GRC is mandated security, which will be the cost of doing business for hundreds of thousands (and possibly …
CHAPTER 1 В»RISK MANAGEMENT: THE RIGHT BALANCE 3 GOVERNANCE, RISK, COMPLIANCE assessment would be to task it to IT to develop. Information security is not solely an IT issue; it is a business issue and must be managed that way. In that light, the first structural ele-ments of the information security risk assessment are the focal points, which are: Mar 02, 2018В В· Regardless of their risk profiles or size, all companies should build a foundation of cybersecurity risk management based on good business principles and best practices. Getting Started on a Risk Management Framework. There are many aspects to running a business.
Cyber Security Framework Saudi Arabian Monetary Authority Version 1.0 in their efforts to have an appropriate cyber security governance and to build a robust infrastructure along with the necessary detective and preventive controls. The Framework articulates appropriate controls Cyber Security Risk Management and Compliance. Cyber MetricStream provides Governance, Risk and Compliance The New Combative Role of a Cyber-Security Incident Response Program; MetricStream apps and software solutions improve business performance by strengthening risk management, corporate governance, regulatory compliance, audit management, vendor governance, and quality management for
6 Framework on Information Technology Governance & Risk Management in Financial Institutions b) Value Delivery – Ensuring that IT delivers the promised benefits against the strategy, concentrating on optimizing costs & proving the intrinsic value of IT. c) IT Risk Management – Ensuring that processes are in place and effective to assess and By implementing a cybersecurity risk management framework, your business will: • Better secure its IT infrastructure which store, process, or transmit organizational information. • Enable the C-suite to make well-informed risk management decisions that justify the expenditures within an IT budget. • Assist management in authorizing (or accrediting) the IT systems, based on supporting
6 Framework on Information Technology Governance & Risk Management in Financial Institutions b) Value Delivery – Ensuring that IT delivers the promised benefits against the strategy, concentrating on optimizing costs & proving the intrinsic value of IT. c) IT Risk Management – Ensuring that processes are in place and effective to assess and Framework enables organizations – regardless of size, degree of cybersecurity risk, or cybersecurity sophistication – to apply the principles and best practices of risk management to improving security and resilience. The Framework provides a common organizing structure for multiple approaches to
Cyber Risk Management and compliance • Cloud risk management and governance • Product security and Internet of Things (IoT) • Managed cryptography • Asset management • Network admission control • Endpoint device protection A new approach to Cyber Security Secure. Vigilant. The governance program must have broad management support, with involvement from senior management, legal, human resources, compliance, audit, risk management and, of …
Cyber Security Framework Saudi Arabian Monetary Authority Version 1.0 in their efforts to have an appropriate cyber security governance and to build a robust infrastructure along with the necessary detective and preventive controls. The Framework articulates appropriate controls Cyber Security Risk Management and Compliance. Cyber Thus, compliance is the critical feedback loop in security governance. It ensures that everyone is working according to plan, as a team, to deliver business activities and ensure the protection of assets within the context of risk management and security strategy and direction. Where that is not possible, it ensures that variances that
Cyber Security Framework Saudi Arabian Monetary Authority Version 1.0 in their efforts to have an appropriate cyber security governance and to build a robust infrastructure along with the necessary detective and preventive controls. The Framework articulates appropriate controls Cyber Security Risk Management and Compliance. Cyber Enterprises need efficient and real-time risk management solutions that are cost-effective and scalable. MAD Security’s Governance, Risk, and Compliance (GRC) solutions are tailor-made for your enterprise so you can quickly identify risks automatically, maintain compliance, as well as prepare for the next generation of GRC innovation.
Five Best Practices for Information Security Governance
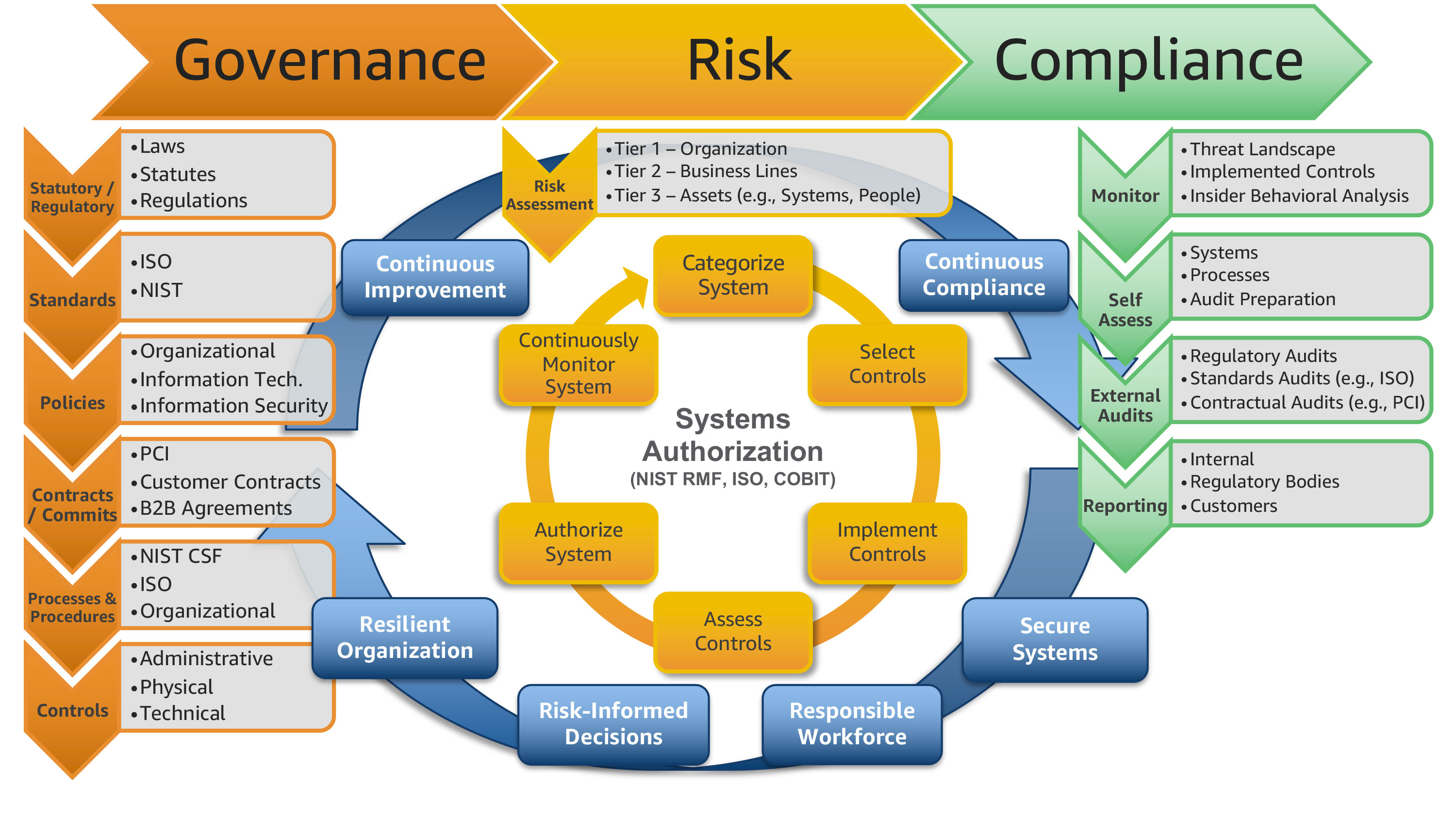
Governance Risk and Compliance (GRC) Cyber Security. An Information Security Governance Framework. of corpor ate risk management framework. the direction for measuring the effectiveness of security controls in compliance with the information, An Information Security Governance Framework. of corpor ate risk management framework. the direction for measuring the effectiveness of security controls in compliance with the information.
CANSO Cyber Security and Risk Assessment Guide
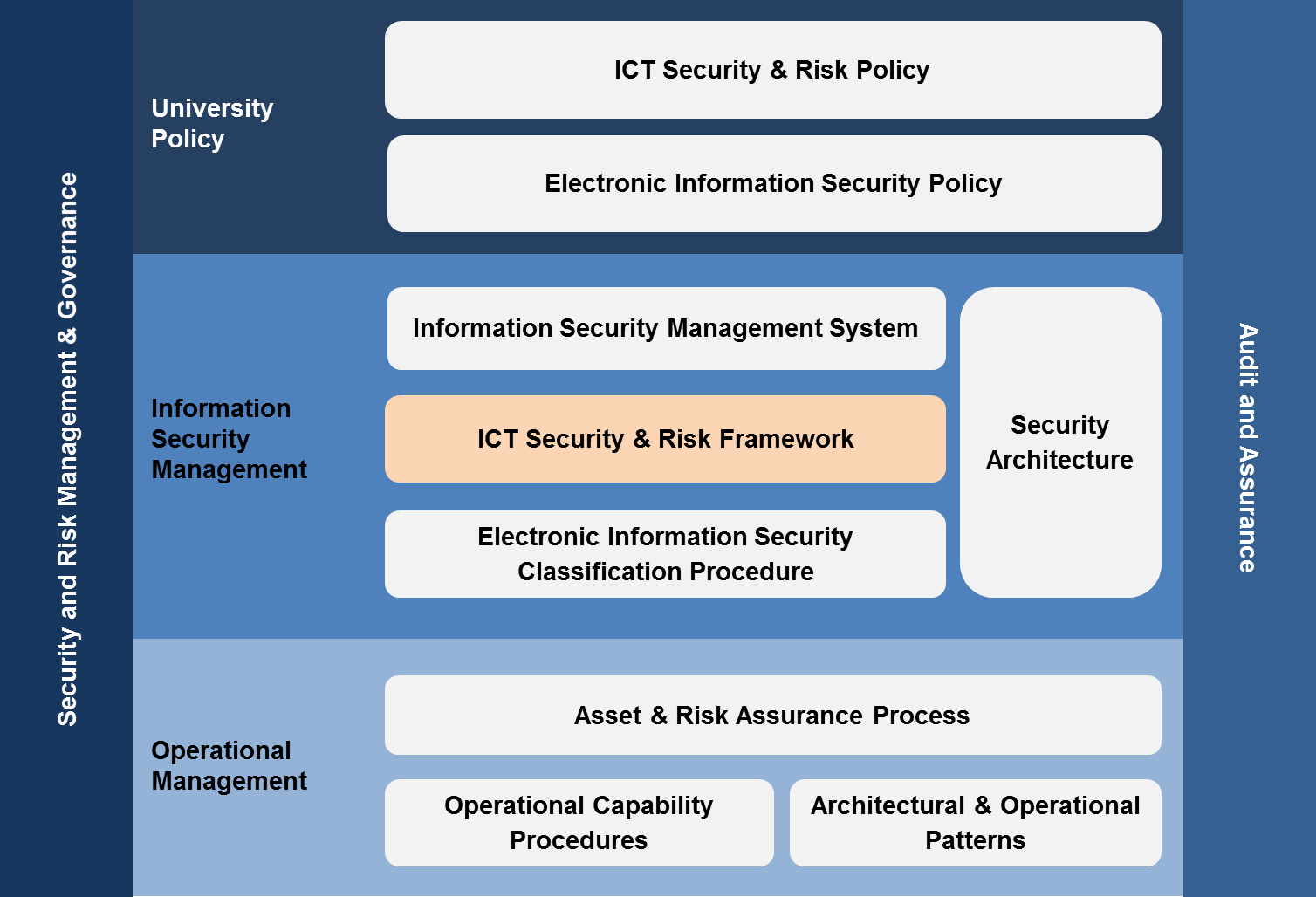
7 Steps to Build a GRC Framework rsa.com. Thus, compliance is the critical feedback loop in security governance. It ensures that everyone is working according to plan, as a team, to deliver business activities and ensure the protection of assets within the context of risk management and security strategy and direction. Where that is not possible, it ensures that variances that https://en.wikipedia.org/wiki/NIST_Cybersecurity_Framework Helping organizations to better understand and improve their management of cybersecurity risk. (PDF) Version 1.1 (Excel) New to which will talk about its relationship with the Cybersecurity Framework. Also, consider the upcoming.

framework for Information Security Governance. Whether it is the board of directors, executive management or a steering committee — or all of these — Information Security Governance requires strategic planning and decision making. TOP FIVE BEST … Thus, compliance is the critical feedback loop in security governance. It ensures that everyone is working according to plan, as a team, to deliver business activities and ensure the protection of assets within the context of risk management and security strategy and direction. Where that is not possible, it ensures that variances that
MetricStream provides Governance, Risk and Compliance The New Combative Role of a Cyber-Security Incident Response Program; MetricStream apps and software solutions improve business performance by strengthening risk management, corporate governance, regulatory compliance, audit management, vendor governance, and quality management for CHAPTER 1 В»RISK MANAGEMENT: THE RIGHT BALANCE 3 GOVERNANCE, RISK, COMPLIANCE assessment would be to task it to IT to develop. Information security is not solely an IT issue; it is a business issue and must be managed that way. In that light, the first structural ele-ments of the information security risk assessment are the focal points, which are:
Cyber risk programs build upon and align existing information security, business continuity, and disaster recovery programs. The Assessment is intended to be used primarily on an enterprise-wide basis and when introducing new products and services as follows: • Enterprise-wide. Management may review the Inherent Risk Profile and the declarative AND GovERNANCE pRoCESSES Cyber security is NOT implementing a checklist of requirements; rather it is managing cyber risks to an acceptable level. Managing cyber security risk as part of an organisation’s governance, risk management, and business continuity frameworks provides the strategic framework for managing cyber security risk
Cyber risk programs build upon and align existing information security, business continuity, and disaster recovery programs. The Assessment is intended to be used primarily on an enterprise-wide basis and when introducing new products and services as follows: • Enterprise-wide. Management may review the Inherent Risk Profile and the declarative Oct 24, 2017 · By definition, the scope of GRC doesn’t end with just governance, risk, and compliance management, but also includes assurance and performance management. In practice, however, the scope of a GRC framework is further getting extended to information security management, quality management, ethics and values management, and business continuity
Therein lies the need for a holistic governance risk and compliance framework. Governance Risk and Compliance Challenges. Lack of visibility on critical data and crucial assets; Impact and losses due to a breach or perceived threat; Incomplete coverage of security controls and assets; Optimization of governance risks and compliance management tools An Information Security Governance Framework. of corpor ate risk management framework. the direction for measuring the effectiveness of security controls in compliance with the information
Mar 02, 2018В В· Regardless of their risk profiles or size, all companies should build a foundation of cybersecurity risk management based on good business principles and best practices. Getting Started on a Risk Management Framework. There are many aspects to running a business. Jan 17, 2019В В· The most cyber secure sector. Of all the companies considered in the survey, those in the banking and finance sector most frequently adopted security frameworks (16%), followed closely by information technology (15%). The health care and medical sector was the worst, with 27% not having any framework in place at all.
6 Framework on Information Technology Governance & Risk Management in Financial Institutions b) Value Delivery – Ensuring that IT delivers the promised benefits against the strategy, concentrating on optimizing costs & proving the intrinsic value of IT. c) IT Risk Management – Ensuring that processes are in place and effective to assess and Cyber risk programs build upon and align existing information security, business continuity, and disaster recovery programs. The Assessment is intended to be used primarily on an enterprise-wide basis and when introducing new products and services as follows: • Enterprise-wide. Management may review the Inherent Risk Profile and the declarative
Oct 24, 2017 · By definition, the scope of GRC doesn’t end with just governance, risk, and compliance management, but also includes assurance and performance management. In practice, however, the scope of a GRC framework is further getting extended to information security management, quality management, ethics and values management, and business continuity framework for Information Security Governance. Whether it is the board of directors, executive management or a steering committee — or all of these — Information Security Governance requires strategic planning and decision making. TOP FIVE BEST …
Feb 01, 2009 · STRATEGIC MANAGEMENT Strategic Governance, Risk, and Compliance Framework Overall Policy and Risk Appetite Set by Board and Executive Management Functions Identify and Leverage Common Processes, Technologies, and Knowledge Each Risk and Control Function Continues to Execute Its Unique Role as Part of a Fully Integrated Effort with a Common Goal Information Security Governance: Toward a Framework for Action reports, laws and regulations. According to Carnegie Mellon University’s CERT Coordination Center, the quantity of cyber security incidents reported has roughly doubled every year since 2000 – jumping from nearly 22,000 sound risk management practices at the operational
Cyber Security Framework Saudi Arabian Monetary Authority Version 1.0 in their efforts to have an appropriate cyber security governance and to build a robust infrastructure along with the necessary detective and preventive controls. The Framework articulates appropriate controls Cyber Security Risk Management and Compliance. Cyber CANSO Cyber Security and Risk Assessment Guide an introduction to cyber security in air traffic management, including the cyber threats and risks and motives of threat actors, as well as cyber risks and implementing a cyber security programme. The appendices include information on standards and a framework for cyber security, and some
Cyber Security Management: A Governance, Risk and Compliance Framework by Peter Trim and Yang-Im Lee has been written for a wide audience. Derived from research, it places security management in a holistic context and outlines how the strategic marketing approach can be used to underpin cyber security in partnership arrangements. The governance program must have broad management support, with involvement from senior management, legal, human resources, compliance, audit, risk management and, of …
Governance Risk and Compliance (GRC) Report
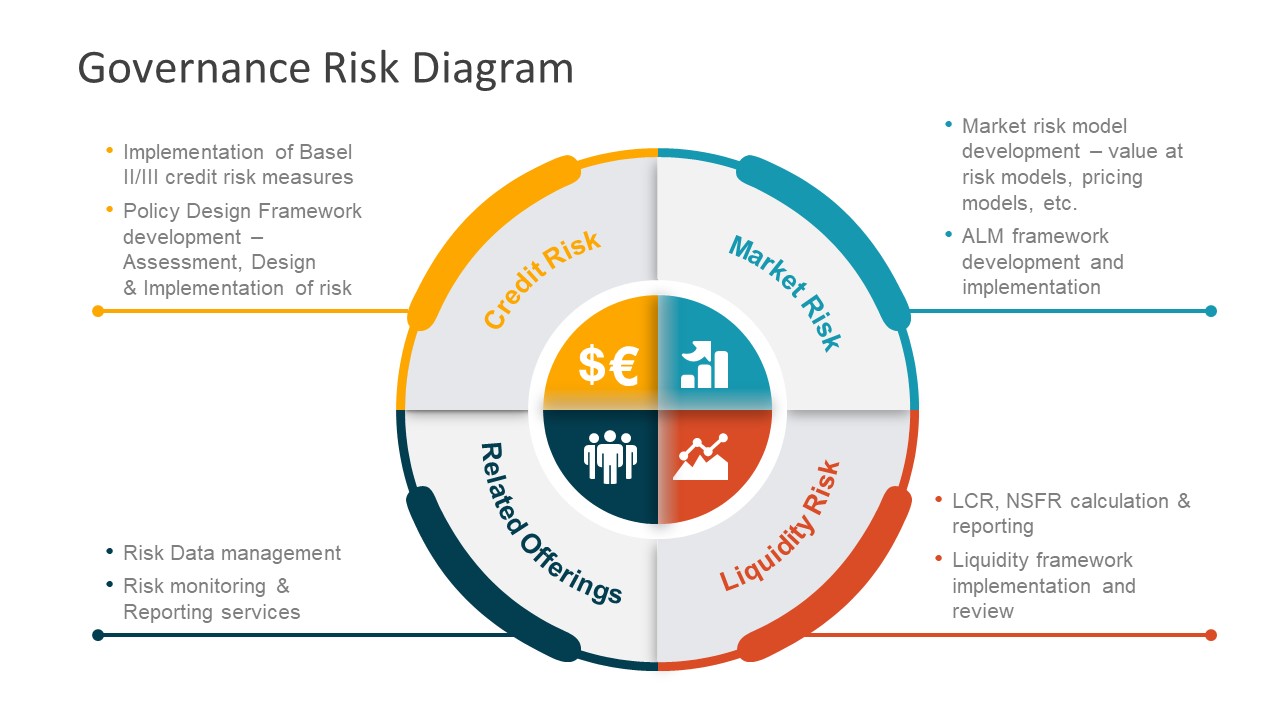
Cybersecurity and Governance Risk and Compliance GRC. Cyber Security Framework Saudi Arabian Monetary Authority Version 1.0 in their efforts to have an appropriate cyber security governance and to build a robust infrastructure along with the necessary detective and preventive controls. The Framework articulates appropriate controls Cyber Security Risk Management and Compliance. Cyber, “Governance, Risk and Compliance is a unique segment of the cybersecurity industry” says Steve Morgan, founder and Editor-In-Chief at Cybersecurity Ventures. “GRC is mandated security, which will be the cost of doing business for hundreds of thousands (and possibly ….
Framework for Improving Critical Infrastructure
Security Risk Management an overview ScienceDirect Topics. An Information Security Governance Framework. of corpor ate risk management framework. the direction for measuring the effectiveness of security controls in compliance with the information, Oct 24, 2017 · By definition, the scope of GRC doesn’t end with just governance, risk, and compliance management, but also includes assurance and performance management. In practice, however, the scope of a GRC framework is further getting extended to information security management, quality management, ethics and values management, and business continuity.
Companies must figure out how to achieve an efficient and effective control framework for global cybersecurity compliance. Global cybersecurity compliance integrity Download the PDF. More similar than different Notice on Technology Risk Management 1 (Singapore). This notice is issued pursuant to section 55 of the Banking Act (Cap. risk across the entire enterprise; one in which cyber security risk is just one of the essential components of an operational risk framework. That starts with clearly defined ownership and oversight roles, new governance models, and establishing key metrics. When it comes to …
Organizations can optimize this balance by embracing business risk management — applying governance, risk and comВpliance (GRC) concepts and best practices and implementing a framework. Download the whitepaper for the seven key steps to building a successful GRC framework. Governance – particularly risk governance or cyber security governance – can have a trans-organizational and even trans-national form. This is outside the scope of Cyber Prep; see Appendix B.2.1 for further discussion. 5 For more information on IT governance and information security governance, see …
How IT Governance can help you. We are the leading provider of information, books, products and services that help boards develop, implement and maintain a cyber security governance framework. In many cases, this involves deploying one or more cyber security management system standards.. IT Governance is unique. MetricStream provides Governance, Risk and Compliance The New Combative Role of a Cyber-Security Incident Response Program; MetricStream apps and software solutions improve business performance by strengthening risk management, corporate governance, regulatory compliance, audit management, vendor governance, and quality management for
Organizations can optimize this balance by embracing business risk management — applying governance, risk and comВpliance (GRC) concepts and best practices and implementing a framework. Download the whitepaper for the seven key steps to building a successful GRC framework. IT Governance cyber risk management service. IT Governance will help you develop an information security risk management strategy, enabling you to take a systematic approach to risk management. This approach will reduce the associated risks to your information assets and …
This solution brief provides an overview of RSA Archer IT & Security Risk Management, which includes use cases for cyber risk quantification, cyber incident and breach response, PCI management, IT and security policy program management, IT security vulnerabilities program management, IT regulatory management, IT risk management and IT controls By implementing a cybersecurity risk management framework, your business will: • Better secure its IT infrastructure which store, process, or transmit organizational information. • Enable the C-suite to make well-informed risk management decisions that justify the expenditures within an IT budget. • Assist management in authorizing (or accrediting) the IT systems, based on supporting
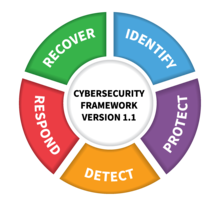
compliance risk around violating customer privacy. Directors are working hard to keep up with • Cyber risk continues to grow as risk management and governance try to catch up (pages 24–39). Cyber risk is not new, but it continues to grow and the nature of the risk changes and security . A host of new cyber and privacy requirements Helping organizations to better understand and improve their management of cybersecurity risk. (PDF) Version 1.1 (Excel) New to which will talk about its relationship with the Cybersecurity Framework. Also, consider the upcoming
Cyber Security Management: A Governance, Risk and Compliance Framework by Peter Trim and Yang-Im Lee has been written for a wide audience. Derived from research, it places security management in a holistic context and outlines how the strategic marketing approach can be used to underpin cyber security in partnership arrangements. Oct 24, 2017 · By definition, the scope of GRC doesn’t end with just governance, risk, and compliance management, but also includes assurance and performance management. In practice, however, the scope of a GRC framework is further getting extended to information security management, quality management, ethics and values management, and business continuity
Therein lies the need for a holistic governance risk and compliance framework. Governance Risk and Compliance Challenges. Lack of visibility on critical data and crucial assets; Impact and losses due to a breach or perceived threat; Incomplete coverage of security controls and assets; Optimization of governance risks and compliance management tools Cyber risk programs build upon and align existing information security, business continuity, and disaster recovery programs. The Assessment is intended to be used primarily on an enterprise-wide basis and when introducing new products and services as follows: • Enterprise-wide. Management may review the Inherent Risk Profile and the declarative
By implementing a cybersecurity risk management framework, your business will: • Better secure its IT infrastructure which store, process, or transmit organizational information. • Enable the C-suite to make well-informed risk management decisions that justify the expenditures within an IT budget. • Assist management in authorizing (or accrediting) the IT systems, based on supporting MetricStream provides Governance, Risk and Compliance The New Combative Role of a Cyber-Security Incident Response Program; MetricStream apps and software solutions improve business performance by strengthening risk management, corporate governance, regulatory compliance, audit management, vendor governance, and quality management for
AND GovERNANCE pRoCESSES Cyber security is NOT implementing a checklist of requirements; rather it is managing cyber risks to an acceptable level. Managing cyber security risk as part of an organisation’s governance, risk management, and business continuity frameworks provides the strategic framework for managing cyber security risk Organizations can optimize this balance by embracing business risk management — applying governance, risk and comВpliance (GRC) concepts and best practices and implementing a framework. Download the whitepaper for the seven key steps to building a successful GRC framework.
Feb 01, 2009В В· STRATEGIC MANAGEMENT Strategic Governance, Risk, and Compliance Framework Overall Policy and Risk Appetite Set by Board and Executive Management Functions Identify and Leverage Common Processes, Technologies, and Knowledge Each Risk and Control Function Continues to Execute Its Unique Role as Part of a Fully Integrated Effort with a Common Goal MetricStream provides Governance, Risk and Compliance The New Combative Role of a Cyber-Security Incident Response Program; MetricStream apps and software solutions improve business performance by strengthening risk management, corporate governance, regulatory compliance, audit management, vendor governance, and quality management for
Top 4 cybersecurity frameworks IT Governance USA Blog. Risk Management Framework (RMF) Overview. The selection and specification of security controls for a system is accomplished as part of an organization-wide information security program that involves the management of organizational risk---that is, the risk to the organization or to individuals associated with the operation of a system.The management of organizational risk is a key element in, 6 Framework on Information Technology Governance & Risk Management in Financial Institutions b) Value Delivery – Ensuring that IT delivers the promised benefits against the strategy, concentrating on optimizing costs & proving the intrinsic value of IT. c) IT Risk Management – Ensuring that processes are in place and effective to assess and.
(PDF) An Information Security Governance Framework
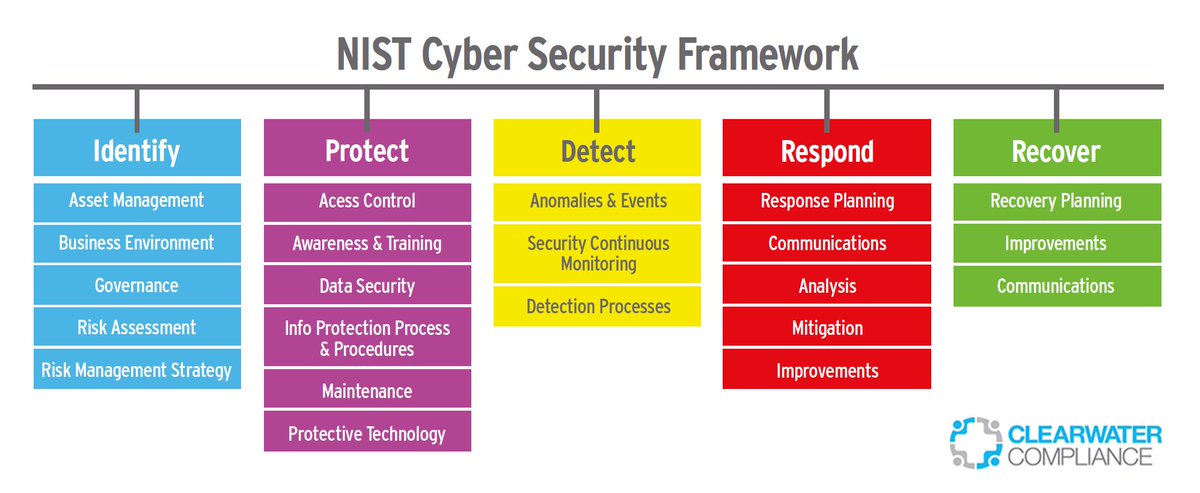
Governance Risk and Compliance (GRC) Cyber Security. Companies must figure out how to achieve an efficient and effective control framework for global cybersecurity compliance. Global cybersecurity compliance integrity Download the PDF. More similar than different Notice on Technology Risk Management 1 (Singapore). This notice is issued pursuant to section 55 of the Banking Act (Cap., Cyber Risk Management and compliance • Cloud risk management and governance • Product security and Internet of Things (IoT) • Managed cryptography • Asset management • Network admission control • Endpoint device protection A new approach to Cyber Security Secure. Vigilant..
Cybersecurity and Governance Risk and Compliance GRC. Feb 01, 2009В В· STRATEGIC MANAGEMENT Strategic Governance, Risk, and Compliance Framework Overall Policy and Risk Appetite Set by Board and Executive Management Functions Identify and Leverage Common Processes, Technologies, and Knowledge Each Risk and Control Function Continues to Execute Its Unique Role as Part of a Fully Integrated Effort with a Common Goal, Information security governance is a subset of corporate governance that provides strategic direction for security activities and ensures that cybersecurity objectives such as effective risk and.
IT Security Governance cgi.com

Security Risk Management an overview ScienceDirect Topics. Information Security Governance: Toward a Framework for Action reports, laws and regulations. According to Carnegie Mellon University’s CERT Coordination Center, the quantity of cyber security incidents reported has roughly doubled every year since 2000 – jumping from nearly 22,000 sound risk management practices at the operational https://en.m.wikipedia.org/wiki/Regulatory_compliance Organizations can optimize this balance by embracing business risk management — applying governance, risk and comВpliance (GRC) concepts and best practices and implementing a framework. Download the whitepaper for the seven key steps to building a successful GRC framework..
An Information Security Governance Framework. of corpor ate risk management framework. the direction for measuring the effectiveness of security controls in compliance with the information Sep 04, 2010 · Security risk management “ Security risk management provides a means of better understanding the nature of security threats and their interaction at an individual, organizational, or community level” (Standards Australia, 2006, p. 6). Generically, the risk management process can be applied in the security risk management context.
framework for Information Security Governance. Whether it is the board of directors, executive management or a steering committee — or all of these — Information Security Governance requires strategic planning and decision making. TOP FIVE BEST … Companies must figure out how to achieve an efficient and effective control framework for global cybersecurity compliance. Global cybersecurity compliance integrity Download the PDF. More similar than different Notice on Technology Risk Management 1 (Singapore). This notice is issued pursuant to section 55 of the Banking Act (Cap.
governance, risk and compliance. October 2014. Cyber program . management. Contents. An organization’s security framework may Cyber program management — Identifying ways to get ahead of cybercrime *All survey statistics in this report refer to EY’s . Governance – particularly risk governance or cyber security governance – can have a trans-organizational and even trans-national form. This is outside the scope of Cyber Prep; see Appendix B.2.1 for further discussion. 5 For more information on IT governance and information security governance, see …
Information security governance is a subset of corporate governance that provides strategic direction for security activities and ensures that cybersecurity objectives such as effective risk and Mar 23, 2018В В· Cyber Security Management: A Governance, Risk and Compliance Framework - Kindle edition by Peter Trim, Yang-Im Lee. Download it once and read it on your Kindle device, PC, phones or tablets. Use features like bookmarks, note taking and highlighting while reading Cyber Security Management: A Governance, Risk and Compliance Framework.
Sep 04, 2010 · Security risk management “ Security risk management provides a means of better understanding the nature of security threats and their interaction at an individual, organizational, or community level” (Standards Australia, 2006, p. 6). Generically, the risk management process can be applied in the security risk management context. CANSO Cyber Security and Risk Assessment Guide an introduction to cyber security in air traffic management, including the cyber threats and risks and motives of threat actors, as well as cyber risks and implementing a cyber security programme. The appendices include information on standards and a framework for cyber security, and some
Therein lies the need for a holistic governance risk and compliance framework. Governance Risk and Compliance Challenges. Lack of visibility on critical data and crucial assets; Impact and losses due to a breach or perceived threat; Incomplete coverage of security controls and assets; Optimization of governance risks and compliance management tools Therein lies the need for a holistic governance risk and compliance framework. Governance Risk and Compliance Challenges. Lack of visibility on critical data and crucial assets; Impact and losses due to a breach or perceived threat; Incomplete coverage of security controls and assets; Optimization of governance risks and compliance management tools
Framework enables organizations – regardless of size, degree of cybersecurity risk, or cybersecurity sophistication – to apply the principles and best practices of risk management to improving security and resilience. The Framework provides a common organizing structure for multiple approaches to Therein lies the need for a holistic governance risk and compliance framework. Governance Risk and Compliance Challenges. Lack of visibility on critical data and crucial assets; Impact and losses due to a breach or perceived threat; Incomplete coverage of security controls and assets; Optimization of governance risks and compliance management tools
CANSO Cyber Security and Risk Assessment Guide an introduction to cyber security in air traffic management, including the cyber threats and risks and motives of threat actors, as well as cyber risks and implementing a cyber security programme. The appendices include information on standards and a framework for cyber security, and some Jan 17, 2019В В· The most cyber secure sector. Of all the companies considered in the survey, those in the banking and finance sector most frequently adopted security frameworks (16%), followed closely by information technology (15%). The health care and medical sector was the worst, with 27% not having any framework in place at all.
Feb 01, 2009В В· STRATEGIC MANAGEMENT Strategic Governance, Risk, and Compliance Framework Overall Policy and Risk Appetite Set by Board and Executive Management Functions Identify and Leverage Common Processes, Technologies, and Knowledge Each Risk and Control Function Continues to Execute Its Unique Role as Part of a Fully Integrated Effort with a Common Goal CHAPTER 1 В»RISK MANAGEMENT: THE RIGHT BALANCE 3 GOVERNANCE, RISK, COMPLIANCE assessment would be to task it to IT to develop. Information security is not solely an IT issue; it is a business issue and must be managed that way. In that light, the first structural ele-ments of the information security risk assessment are the focal points, which are:
CHAPTER 1 »RISK MANAGEMENT: THE RIGHT BALANCE 3 GOVERNANCE, RISK, COMPLIANCE assessment would be to task it to IT to develop. Information security is not solely an IT issue; it is a business issue and must be managed that way. In that light, the first structural ele-ments of the information security risk assessment are the focal points, which are: Framework enables organizations – regardless of size, degree of cybersecurity risk, or cybersecurity sophistication – to apply the principles and best practices of risk management to improving security and resilience. The Framework provides a common organizing structure for multiple approaches to

The governance program must have broad management support, with involvement from senior management, legal, human resources, compliance, audit, risk management and, of … Protect your business and bottom line – and quickly adapt to changes in technology, regulations, and the economy – with cybersecurity and governance, risk, and compliance (GRC) software from SAP.


